Prevent Credential Leaks with Secrets Detector
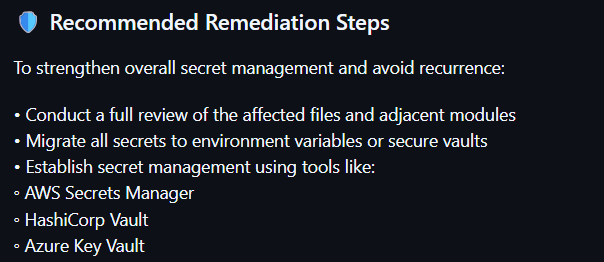
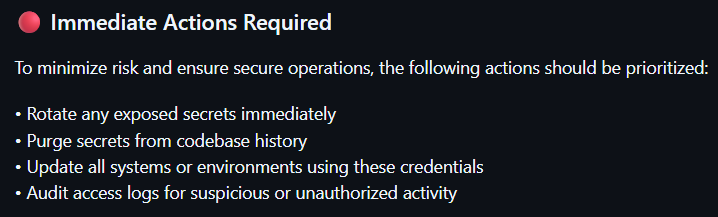
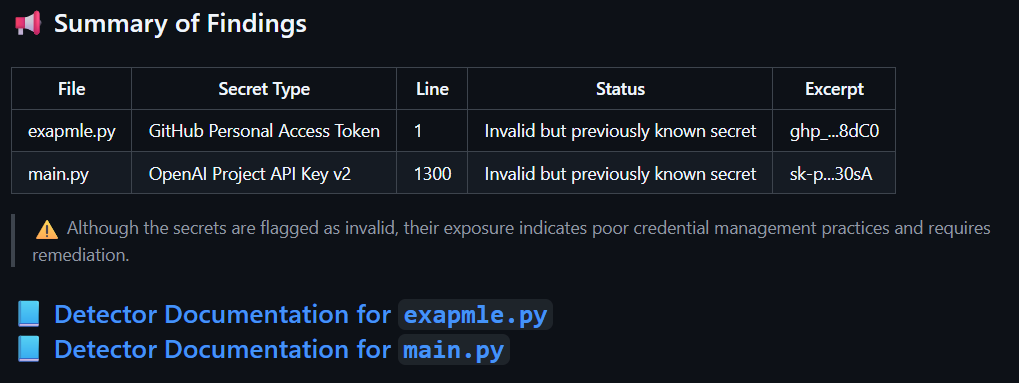
One of the most overlooked but critical security risks is the accidental exposure of secrets in code—API keys, access tokens, passwords, and private credentials. Our Secrets Detector tool scans your repositories to uncover sensitive data before it leads to unauthorized access or data breaches.
Detect Secrets